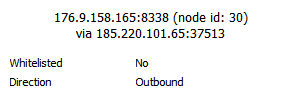
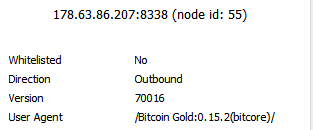
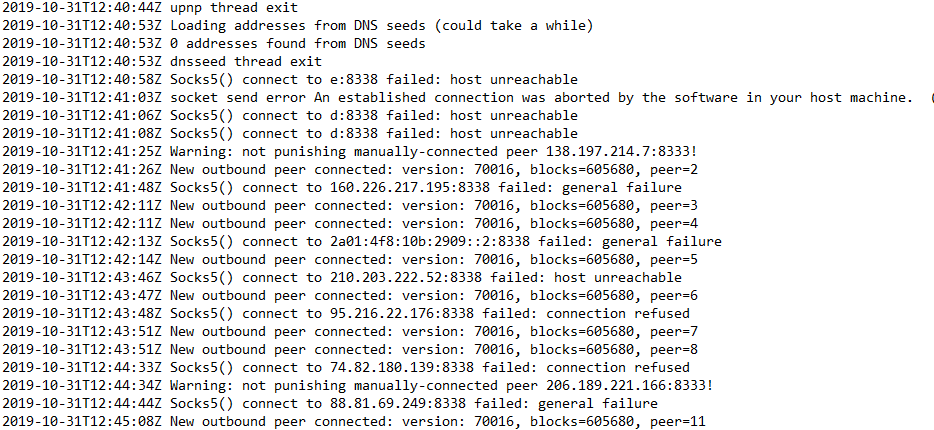
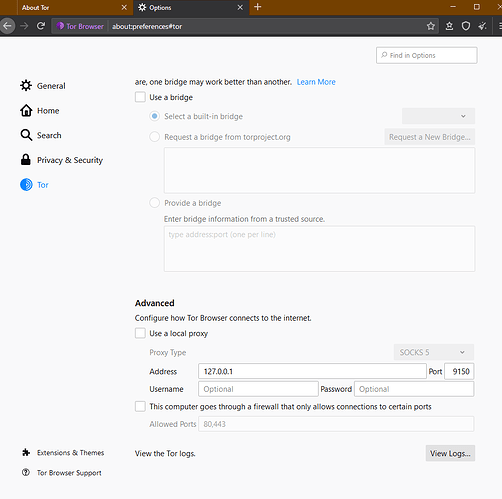
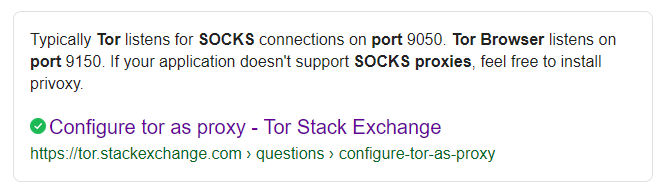
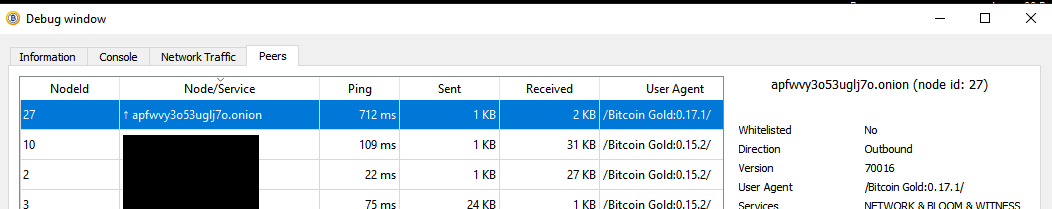
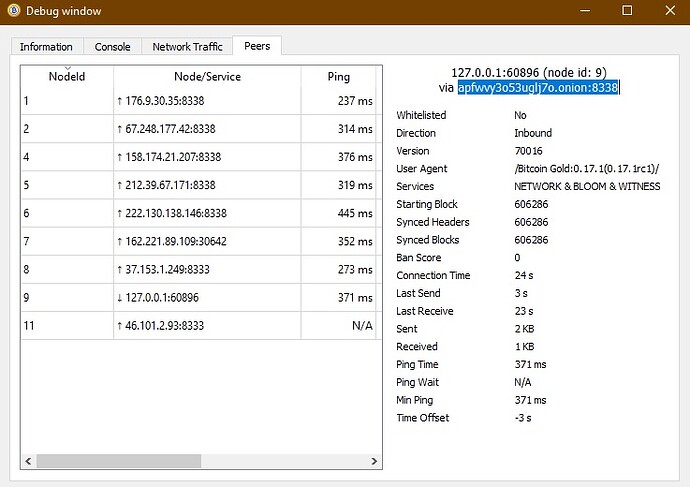
That is someone else, my nodes are all 0.17. Also, that’s not a .onion address, it’s just an IPv6 instead of IPv4.
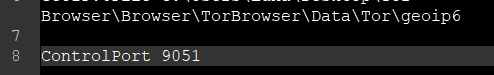
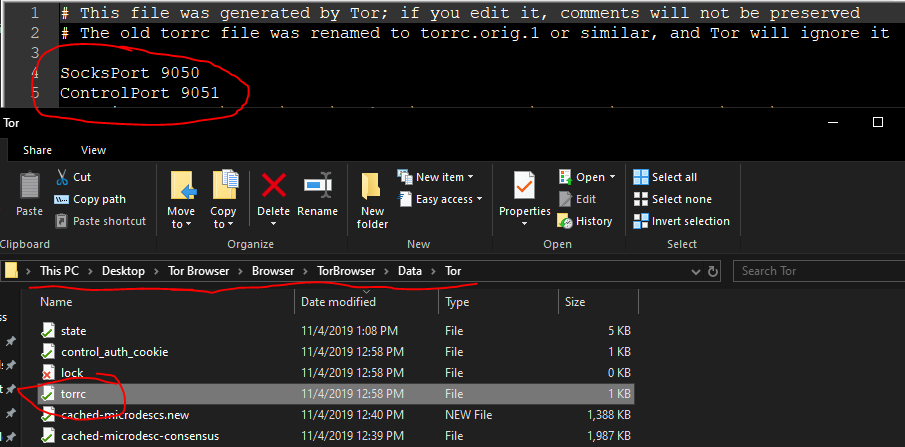
I made only one change in Tor browser. I added the following line in my torrc file:
ControlPort 9051
You still haven’t said whether you’re running Nix, Mac, PC… on Windows, the torrc file is in Tor’s installation folder, here: Tor\Browser\TorBrowser\Data\Tor\torrc.
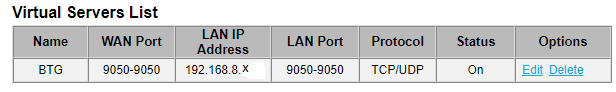
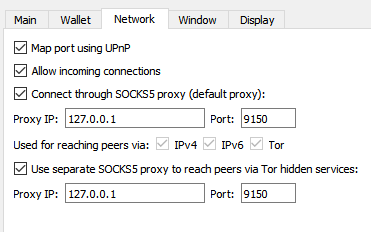
The default ControlPort for Tor Browser is 9151; if you run a router providing Tor for all devices on your network, the default ControlPort would be 9051. The BTG Node is looking for that. I found no way to change that in the BTG Node, so I changed it in Tor Browser.
Try that, restart Tor Browser, kill BTG, delete the debug.log, start BTG, and then look for this after a minute:
2019-10-31T04:18:29Z torcontrol thread start
2019-10-31T04:18:29Z tor: Reading cached private key from D:\BitcoinGold\onion_private_key
2019-10-31T04:18:29Z tor: Successfully connected!
2019-10-31T04:18:29Z tor: Connected to Tor version 0.4.1.6
2019-10-31T04:18:29Z tor: Supported authentication method: COOKIE
2019-10-31T04:18:29Z tor: Supported authentication method: HASHEDPASSWORD
2019-10-31T04:18:29Z tor: Supported authentication method: SAFECOOKIE
2019-10-31T04:18:29Z tor: Using SAFECOOKIE authentication, reading cookie authentication from C:\Users\Luna\Desktop\Tor Browser\Browser\TorBrowser\Data\Tor\control_auth_cookie
2019-10-31T04:18:29Z tor: SAFECOOKIE authentication challenge successful
2019-10-31T04:18:29Z tor: AUTHCHALLENGE ServerHash 6985e673add8293820ab1ff2abc978b596b2805acb892bec8645e7f7c01e0052 ServerNonce e5244de74bb33f13af1be3538e6f326986de15e9dfd349a7caa5d71851b005f8
2019-10-31T04:18:29Z tor: Authentication successful
2019-10-31T04:18:29Z tor: ADD_ONION successful
2019-10-31T04:18:29Z tor: Got service ID lionkkmdd4n4rx5h, advertising service lionkkmdd4n4rx5h.onion:8338
2019-10-31T04:18:29Z tor: Cached service private key to D:\BitcoinGold\onion_private_key
2019-10-31T04:18:29Z AddLocal(lionkkmdd4n4rx5h.onion:8338,4)
2019-10-31T04:18:29Z AddLocal([2001:0:2841:f634:804:13c1:93cd:b49]:8338,1)
2019-10-31T04:18:29Z Discover: Tanden - 2001:0:2841:f634:804:13c1:93cd:b49
2019-10-31T04:18:29Z upnp thread start
2019-10-31T04:18:29Z Bound to [::]:8338
2019-10-31T04:18:29Z Bound to 0.0.0.0:8338
A few lines later, it starts opening connections and I see my first outbound connection through Tor:
2019-10-31T04:18:29Z opencon thread start
2019-10-31T04:18:29Z addcon thread start
2019-10-31T04:18:29Z trying connection 123.114.40.9:8338 lastseen=0.0hrs
2019-10-31T04:18:29Z GUI: initializeResult : Initialization result: true
2019-10-31T04:18:29Z GUI: Platform customization: "windows"
2019-10-31T04:18:29Z SOCKS5 connecting 123.114.40.9
2019-10-31T04:18:29Z SOCKS5 sending proxy authentication 0:100:
If not getting detail in your debug log, add:
debug=1 (in bitcoingold.conf)
You do need to make sure to whack your debug.log from time to time - it will grow huge!
You also have the option of debug=tor, also, but I find the other info useful.
(Also, if you’re running BTG 0.15.2, get 0.17.1rc1 instead.)
What is this Node that you’ve manually connected to? Maybe you should take it out of your .conf file?
If you’re sure it’s a valid BTG node, then something very weird is happening. It shouldn’t be behaving in a way to make your node want to punish it.